In Tom the register area is not very big and consists of very few memory locations then a modern Intel Pentium computer. The speed of the Intel Pentium computer depends on how many bit the computer has and the higher the bits ,the faster the computer operates.
PROGRAM COUNTER
The program counter can be described as a list of rules and instructions needed by a computer to perform its functions and tasks. These functions and tasks are explained to the computer with the help of programming languages like JAVA,C++ or SQL. These languages are used by computer programmers to make different software to run a specific task or function. The computer translates these programming language into its own language which it can understand.
ACCUMULATOR
The Accumulator consists of all the universal or intermediate results that the computer accesses when a result is needed. These universal results may consists of mathematical calculations ,like multiplication, addition or subtraction .The computer looks in the accumulator to find results of mathematical calculations rather then write the results on the hard drive and then read it from the drive .
Tom also has accumulators which help Tom to perform several instructions by accessing the accumulators when needed.
STACK POINTER
Stack pointer is a special type of data structure in which items are removed by the most recent added item deleted first. So the deletion is done on the basis of the order they were added .
“Pushing ” is a term used when an item is added to a stack .Similarly deleting of items is called “Popping”
STATUS REGISTER
Status register is like a register which keeps details of all the data that the hard drive of a computer is holding. The computer in order to save time looks for data in the status register when it needs processing rather then searching the whole of the hard drive. The status register tells the computer which location of the hard drive the data is stored.
The speed of the computer depends on the amount of registers the computer consists of .Higher the registers ,higher is the speed of the computer to perform functions and tasks. The number of registers are called Bits for example 32 bit ,64 bit .
ADDRESS
As explained before ,the hard drive of a computer can be divided in to small parts called bytes. These bytes store the data that the hard drive stores. Each byte has an address that is kept in the register of the computer.
The computer looks in the register for the address for the required data and then goes to that location of the byte in the hard drive.
In Tom the number of addresses required will depend on the data it is holding in the storage area .
In an Intel Pentium the number of addresses also depend on the size of the hard disk and any other storage devises and how many bytes do they consist of.
DATA LINES
Data lines are the layers of hard drive that is used to store the functions and information the computer needs to operate .The type of data stored may vary depending on if the data is a text file or a program file.
In Tom the data lines are the different layers of blocks where information can be stored in the memory location. Tom has 80 memory locations and therefore the amount of data lines would be 80 times the amount of data lines each memory location has .
In a Intel Pentium however the data lines are many depending on the size of the hard drive.
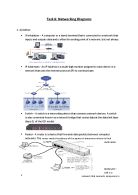
NETWORKING AN INTERNET COMPANY
The internet company needs to be networked internally as well as both the offices to be linked as well. In order for the company to do this ,it will need a lot of very expensive equipment which I will be explaining as following
NETWORKING INTERNALLY
In order for both the offices to be linked together ,the company needs the following equipment.
LOCAL AREA NETWORK
A local area network will be needed to link the different computer stations within each office.
Local area network consists of usually one server per office and can attach many number of office desk tops with the server in each office. It also provides security as well in the shape of network security .This security provides the network to have login passwords and user accounts with different restrictions depending upon the type of user. This network also provides users to access data files that they are privileged to access and not the ones that they are not allowed to access.
The LAN will also allow the staff in both the offices to share data files and other data with other staff on different workstations within the same office. Peripherals can also be shared amongst staff, which could save the company a lot of money.
ETHERNET
Ethernet is a LAN topology, which will be used to wire the different workstations within each office to each other. It operates with a speed of 10megabits per second and is easy to install. Ethernet also has its own form of collision detection ,which can allow peripherals to run on the same cable. It can also connect more then 1000 workstations with the help of TCP/IP addresses of each workstation. One advantage of this topology is that data can run in each direction thus linking the different workstations together.
BRIDGING
Bridging is a method which would connect the two LAN ‘s together in each office and would allow the staff to share data and peripherals. Using bridging will help to move data between the networks of each of the offices.
Bridges is very easy to use as well as it only needs to be plugged in .
NETWORKING EXTERNALLY
The company needs the following equipment to link both the offices together
WIDE AREA NETWORK
This will be used so that staff can work form home .The staff will be able to access computers simultaneously through the same physical medium.
A web site will be needed as well so that both the offices will be linked together and also staff at home can go on the internet and access all the data that they need to access.
PACKET SWITCHING
This is also a wide area network in which the wan devises share a single point to point link to transport packets from a source to a destination across a network. Each switch may connect to more switches or computers. It also stores incoming packets. Packets switching has internal memory and it can hold a packet if the outgoing connection is busy and the packets for each connection are held on a queue.
Packet switching will also allow the staff to transfer data among each other.
UTP
UTP stands for unshielded twisted pair ,which is used to connect coaxial cable. It is very cheap to buy and install and requires the purchase of components like computers .
HUBS
A hub is the central point where twisted pair coaxial cables are connected to facilitate central management for the system. They are electronically powered to connect the signal flowing on the cable. The company will use the hub by extending LAN and then it will pass the data further down the signal. The hub will also help the business to build internet networks.
SERVER
A server is a work station that connects all the workstations together .All the management tools are on the server and are used to help install things like network printers and security policies.
The company will have at least one server in each location of the two offices and all the workstations will be linked together with the help of these two servers.
MODEMS
Modems are used to link the computers with the internet with the help of a telephone line .These modems will be used by the offices to work from home and also to transfer data between the two offices and will link the workstations in both the offices. One draw back of modems is that they are very slow and it takes a lot of time to transfer data between different workstations.
BROAD BAND
This is a very new internet technology and is also used to connect the computer with the internet .The speed is also very fast thus allowing the staff to transfer the data very quickly and efficiently. But broad band is very expensive compared to the modems and cost about 25 pound a month for a 1 gig connection speed.
USB
This is a universal serial bus and connects computers and peripherals .USB will help the company in digital imaging .Cameras can be connected with the computers and data can be transferred .It is very easy to install and easy to use .USB connectors will allow the staff to attach printers and other devices.
FIREWIRE
Firewire puts in to effect an access control policy between the two networks .It also has essential role as a security blanket for the management by alerting the management of any security breaches ..The firewalls purpose will be to keep hackers out of the computer networks .
It also provides security for using the internet. It is very cheap and is easy to install.
PCMCIA
PCMCIA stands for personal computer memory card international association which is a small computer consisting of PC cards. They are designed for adding memory to portable computers. PC cards will help the business by transferring data and adding ROM and RAM in to the personal computer. The firm will also be able to change the card to a modem card without rebooting the system.
BACKUP SYSTEM
Back up is a process where all the data is stored in a different location from the main storage area so that data will not be lost if the main storage device stops working. A company needs to keep and update backup files on a regular basis if it needs to make sure that all its data is safe from being lost. The company will have to have back up computers or hard disks to store data all the time.