2.
3. A)
Possible Future needs DingoMobile:
- Expanded Servers (Multiple Head/Smaller Offices).
- Expansions – New Stores/Offices
- New Workstations/Peripheral Device
LAN –
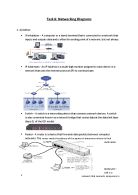
Currently, Dingo Mobile has a single store, and a head office. Each individual premise would require a network. The LAN network would allow this; we could connect all the workstations and various other devices (including servers for the Head Office). The LAN network is better described in part 2, basically being a physically connected network on each of the individual premises. Through doing this, we would be able to create a physically network that allows for an individual network, and then also allows the LAN network to interact with the other stores through the VPN.
Justification – Taking into consideration the fact that most of DingoMobile’s stores will probably want to use more than one workstation, so creating a LAN network on each premise will cater for this, and then allow each of the connected workstations to also access the internet. The LAN will also allow each store to utilize other peripheral devices, such as printers, which I’d assume would be required for some activities on the premises.
How LAN fulfils future needs – LAN’s are ‘relatively’ simple to set up, obviously they can utilize a ‘WLAN’ (Wireless LAN), if setup becomes a problem. The LAN will cater for any expansions each individual store/office requires; all that is needed is another cable to connect the workstation/peripheral into the LAN network. This also gives DingoMobile the reassurance that any required expansions to the network are basically a cable connection away.
Considerations for the LAN – The LAN aspect of this network solution may not be as effective, if some premises find it difficult to run cables connecting all of their computers/peripherals together. This should be solved however if they can utilize a WLAN instead, however that is only a possible solution if they cannot run wires throughout the premises.
VPN –
Currently, Dingo Mobile has a single store, and a head office. They require a connection between each of the stores/head office, allowing networking between each of the stores/head office. The VPN would allow this; we would connect each of the individual LANs to a Cable/DSL Model that would then allow connection to the internet and from that, access to the Dingo Mobile VPN. The VPN network is better described in part 2, basically being a private network utilizing public telecommunications (the internet). Through the VPN, we will be able to connect each of the store’s LANs together, allowing for wider-scale networking for the Dingo MobileCompany.
Justification – Taking into consideration that Dingo Mobile desires a connection between the store and the head office, I’ve selected a VPN network to cater for this. The VPN will allow DingoMobile to create a ‘universal’ network, and allowing the potential future stores to be connected also.
How VPN fulfils future needs –The VPN utilizes the internet, therefor it isn’t going to restrict the possible expansions that DingoMobile may require (being one of their future needs). If ever Dingo Mobile requires the sending of important data between head office/stores, the VPN will ensure that the data sent is encrypted, catering to the potential need for safety of transferred data.
Considerations for the VPN –The VPN should operate fine, and should continue to do so into the future. Since the VPN is created using the internet, so obviously things such as bandwidth, speed etc., may become an issue. Measures however can be taken to speed up the VPN, so it isn’t a vital issue that needs to be worried about.
3b)
Development Process – The existing system, from the information that I have been provided, basically includes no real networking (The information provided doesn’t indicate whether the store/office have actual networks setup individually, so I’m going to assume that they do not). Basically, DingoMobile want a networking solution to connect all of their store(s) and Head Office together, and I’ve explained the majority of this networking solution in the past two parts of this ‘report’.
An overview of how the new system would be implemented, replacing the old system -
- If any previous network is set up on the individual premises, I would recommend taking it apart, and starting from scratch to ensure that everything is following the new network solution.
- Check that every workstation is clean from viruses/non-corrupted and doesn’t have data that the entire future network should have access to.
- Set up all of the workstations/other required devices in both the store and Head Office.
- Connect all of the devices in each premises to the router, and each router to the modem (Setting up the LAN).
- Once both LAN networks have been established, ensure that both are also connected to the internet.
- Now that all of the LAN networks have been set-up, it would just be a matter of creating the VPN and interconnecting the head-office and all of the stores.
- Test the VPN to ensure that everything is working, and once this is finished. The network should be ready for use! Also set different privileges for different users, ensuring that not everybody has access to everything within the network.
Also, I’m explaining a quick overview of the Business’s expansion; this includes how the network will expand.
- Once the network has been setup for the Head Office and single store, it will then be in the state to expand upon if required.
- Whenever a new peripheral device requires to be added into the network, it will be connected through the LAN of the premises that it is situated, then also from that will be connected to the VPN.
- Whenever a new store is established, a similar LAN network will be created on the premises, and from there all of the software related set-up will take place that allows that LAN network to also access the DingoMobile VPN.
- Whenever a new Office is established, it will follow the same steps as the store; however a server may also be included into the LAN setup.
As you can see, it’s relatively simple for the Business to expand with the current Network Solution I have provided.
3c)
Monitoring the Network – To ensure that the employees are utilizing the network for work purposes, and also to monitor what is being sent throughout the network/occurring throughout the network (including potentially malicious activity etc) is a necessity for DingoMobile. Below are some methods that can be used to monitor the network –
-
UserMonitoringSoftware–This will be a vital part of monitoring the network, the users may be inclined to utilize the network for activities that aren’t helping/causing troubles for DingoMobile, so installing software that monitors all of the employees activity (to an extent that doesn’t conflict with personal privacy) would be one way to monitor the network.
-
Users/Groups – It’s recommended that the users/groups of the network is monitored regularly, due to potential ‘hackers’ gaining access into the VPN and assigning their new user all of the permissions, becoming a security problem for your network.
-
FilteringcertainURL/emails – This will allow you to hopefully avoid malicious files/sites being accessed through the network.
-
Enabling Firewalls (Monitoring the Web Access at Firewalls) – This builds onto the filtering URL/certain emails/files that are sent or accessed throughout the network. It allows you to monitor exactly what is being filtered, and keep track of related activity.
EvaluatingtheNetworkSystem –Methods must be utilized to also evaluate the health, speed and general performance etc. of the network, these methods will be used to evaluate the network system in periodical intervals, indicating to the business when and where maintenance must occur on the network system.
-
Benchmarking – Certain programs can be used to compare the network against others in terms of performance. This would be a good indication to how DingoMobile’s network compares to other, similar networks.
-
CheckingtheNetworkUsage – There are tools that the administrators can use, such as the ping function, to measure the network usage, and also the Round Trip Time. This can be a good indication to how the network is performing.
-
Reading through related Error Logs – Reading the error logs relevant to the network will enable the reader to detect any issues, big or small, that may be occurring within the network. Checking this periodically will hopefully enable Dingo Mobile to pick up any problems occurring within the network.
-
Testing the Speed of the Network – Sending files from one premise to the other using the VPN aspect of the network can be used to test the speed of the network, and this can then highlight if there is any issues such as packet-loss that are occurring, and hopefully allows DingoMobile to then find and solve these problems.