Designing a data system for a vintage clothes business.
Ross KennedyCandidate Number: 0518Centre Number: 22151 Computing Coursework Analysis Contents Computing Coursework . Introduction .1. Client Identification .2. Define the current system .3. Describe the problems .4. Section appendix 2. Investigation 2.1. The current system 2.1.1. Data sources and destinations 2.1.2. Algorithms 2.1.3. Data flow diagram 2.1.4. Input Forms, Output Forms, Report Formats 2.2. The proposed system 2.2.1. Data sources and destinations 2.2.2. Data flow diagram 2.2.3. Data dictionary 2.2.4. Volumetrics 3. Objectives 3.1. General Objectives 3.2. Specific Objectives 3.3. Core Objectives 3.4. Other objectives 4. E-R Diagrams and Descriptions 4.1. E-R diagram 4.2. Entity Descriptions 5. Object Analysis 5.1. Object Listing 5.2. Relationship diagrams 5.3. Class definitions 6. Other Abstractions 6.1. Graphs 7. Constraints 7.1. Hardware 7.2. Software 7.3. Time 7.4. User knowledge 7.5. Access restrictions 8. Limitations 8.1. Areas which will not be included in computerisation 8.2. Areas considered for future
Compare the relative advantages and disadvantages of bitmap and vector image types.
Compare the relative advantages and disadvantages of bitmap and vector image types. Graphics are drawn using either bit-mapped programs such as Paint or vector programs such as Autosketch, both of which have their advantages and disadvantages. A bitmap is an image which is made up of tiny squares of colour. They produce good quality image where shading and fine detail are needed such as in photographs. The amount of detail that can be seen in a picture depends on the resolution of the image; how many times per inch these squares or pixels occur. 300 times per inch is what is needed for good quality reproduction on a commercial printing press, and 72 pixels per inch for monitor display. The main advantage of a bitmap is that it can be accessed sooner through the internet when you have the proper size. The accuracy is very high when displaying image information including the shadings and the other complex and smooth places. Another advantage is that it can be used as a universal format. Most of the Bitmap graphics are not proprietary. One of the disadvantages associated with a bitmap image is that it does not tend to resize very well. While it may be easy to scale down an image without loss of clarity, it is not easy to enlarge the image, can result in aliasing because of the 'pixelation' makes the image look coarse. Another disadvantage associated with a bitmap is the
HCI shortened for Human Computer Interaction is the study of the human and computer and the way they interact. The interaction between human, whom may be referred to as users and the computer occurs at the users interface
P1 - Describe the impact of HCI on society, the economy and culture. Introduction HCI shortened for Human Computer Interaction is the study of the human and computer and the way they interact. The interaction between human, whom may be referred to as "users" and the computer occurs at the users interface, which simply means the way you input and output information. Society; The first interface that I will be looking at and its effect on Society is the online shopping - EBay. EBay is one of the world's online marketplaces with a global customer base of 233 million. EBay has created a powerful marketplace for the sale of goods and services by a passionate community of individuals and small businesses to exhibit. Below is an image of EBay. EBay offers different features such as allowing customers to create an account for its users, it gives clear stated categories in which people can easily search from and it markets people's product on the front page to advertise their product. It's impact on Society; EBay has impacted the society in the sense that people can now shop online with ease and not having to go out of their way to locate a shop to purchase items. It has given people opportunity to market their business and product. It also enables its user to communicate with one another for transaction. It has brought people from across the globe to purchase items and
Organisational system security - The possible security issues which exist within the FilmPoster.com system
The possible security issues which exist within the FilmPoster.com system M1 DoS attack: a DoS attack is an attack a person that hacks a computer in an attempt to make computers resources unavailable to its intended users. Though DoS attacks motivation may be carried out for different reasons. Film posters have a web site used to sell movie posters to collectors and a DoS attack will be used by the attacker to prevent the film posters site from functioning efficiently, temporarily or indefinitely. Since film posters hold details of their customers, who have registered with the website, with websites that hold such information people that use DoS attacks target such sites or services hosted on web servers. The attack can be used to saturate the targets machine, such that it cannot respond to legitimate traffic, consume its resources so that it can no longer provide its intended service. They are so many different ways of using DoS attacks they basic types of attacks are, disruptions of physical network components, obstructing the communication media between the user and the film poster from communicating adequately. They can also use Permanent Denial of Service Attacks: a denial service attack attacks and damages a system so badly that it will require replacing or reinstalling the hardware. Phishing attackers; will attack filmposters.com website to acquire sensitive
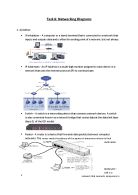
Networking Diagrams and Case Study
Task 6: Networking Diagrams . A) Define: . Workstation – A computer or a dumb terminal that is connected to a network that inputs and outputs data and is often the ending point of a network, but not always. 2. IP Addresses - An IP Address is a multi-digit number assigned to each device in a network that uses the internet protocol (IP) to communicate. 3. Switch – A switch is a networking device that connects network devices. A switch is also commonly known as a network bridge that routes data at the data link layer (layer 2) of the OSI model. 4. Router - A router is a device that forwards data packets between computer networks. The router reads the address of the packet to determine where its final destination. 5. WAN/LAN – LAN is a network that connects computers in a smaller area such as a home. The difference between a LAN and a WAN are that a WAN is when two LAN’s are connected with a LEASED line that connects them. 6. Firewall – Can either be software or hardware-based and is used to help keep a network safe. Its main objective is to control the incoming and outgoing traffic as it analyzes the data packets and determining whether it should be allowed through or not. 7. Server/Proxy Server – operates on layer 7, 6, 3 of the OSI model 8. Star Network – One of the most common network topologies. A star network has one central switch/hub/computer, which
Why its important to have protocols and standards on a network
To: Peter Cresswell From: Kyle Jones Date: 30th April 2012 Message Protocols are important on a network because without protocols computers would not be able to talk to each other and so the internet would be useless. For example if you are in France, and did not speak French you would not be able to talk to anyone because you wouldn't be able to understand them, and they could not understand you if they did not speak your language. This is the same for Internet protocols. If one computer wants to talk to another then they would need to understand the same protocol. So basically Protocols are the rules that allow communication between two or more computers. The main internet protocols are; HTTP (Hyper Text Transfer Protocols) HTTP helps us display webpages. If the computer did not know this protocol, then you would not be able to view the webpage because the computer would not understand the code used and so it would be unable to display the webpage. FTP (File Transfer Protocol) FTP helps us send and receive files sent from other computers. If either of the two computers did not understand this protocol then you would not be able to send and receive files because the computer would not know the "language" and so sending a file would be impossible. SMTP/POP3 (Simple Mail Transfer Protocol & Post Office Protocol) SMTP and POP3 is the protocol for sending
LAN & Topologies & Data Flow
BTEC National Certificate for IT Practitioners Unit 8 Communication Technologies Assignment 3 Introduction In this assignment I am going to list and describe the components that make up a LAN. I will also state how they can be interconnected and interact with each other. I will show some LAN topologies and illustrate them. Finally I will explain and describe how data travels around the various topologies and list the advantages and disadvantages of each topology. LAN I am going to look at the components that make the LAN and describe them. Ethernet, Hardware, NIC's, Hubs/Switches/etc these are the list of components that make up the LAN and now I am going to explain each of these components. NIC's - Network Interface Card are used for connecting a RJ-45 cable. Nearly all the modem PC's or PC's which connect through dial-up connection need a NIC. On either ends is a RJ-45 connector which then allows you connect to another computer on the network or another device. The NIC is interconnected to other hardware such as the motherboard; this allows it to communicate with the computer. There are 3 ways the NIC can be connected to the computer. As mentioned before it can be integrated on the motherboard, connected through a PCI slot or connected using a ISA slot (Industry Standard Architecture). For the NIC's to communicate with each other properly they need to have been
Business & IT Department BTEC. Organisational System Security - Describe the various types of threats to organisations, systems and data
Assignment 1 Describe the various types of threats to organisations, systems and data - P1 * Unauthorised access - This category covers internal and external threats. Internal threats are things such as: Magic Disks - A recovery or backup disk that has been modded to include viruses or key loggers. Man in the middle attacks - People extracting sensitive and confidential information whilst posing to be a customer, or a legitimate company. Implanting Key loggers - Applications designed to record key strokes and send them back to the hacker. External threats are this such as; Viruses - Rouge applications designed to damage or make a system vunerable Trojans - Applications designed to infiltrate a system often by posing to be a harmless file or embedded into another file. Piggybacking - A term given to people who use someone else's internet connection without authorisation. This is often undertaken by logging onto an unsecured network without permission. Phishing - Attempting to fool a user into believing you are a legitimate service attempting to gain sensitive information. * Damage to or destruction of systems or information Damage to systems can occur when devices fail such as hard drives failing or natural disasters occurring in the workplace that could result in damaged or destroyed places. Such as: . Natural Disasters: This refers to what happens when data is
Utility Programs and Macros
Utility Programs Definition: A utility program is a program that performs a common task, such as copying and listing files on a list. Utility programs are generally provided alongside the operating system, but are sometimes bought separately. Many utility commands change with the operating system. Eg. In windows, the copy command is Ctrl + C, but in Mac OSx this changes to Command +C. The major tasks carried out by utility programs are: ) Disk Formatting (Preparing either laser or hard discs for use) 2) Listing files in directories or folders. 3) Copying files, either from application to application, or within the same application. (Web browsers, word processors) 4) Copying discs 5) Renaming files 6) Backing up files, and also creating OS backups. (Time machine (Mac OSx), Windows Backup) 7) Running a file search in large files or directories Some other major tasks which operating systems often, but not always provide are: ) File and Disc repair [Check disk, Defragmenter, Disk utility (Mac OSx)] 2) Anti-Virus tools, or malware checkers. (Windows Defender, Mac Cleaner) 3) Web Browser, to surf the internet. This could be standard, purchased, or freeware. (Safari, Internet Explorer) 4) File Compression, to compress files, and make the file size smaller. (Windows File Compression, Mac file Compression) Note: Often, these tools are not given by the Operating System,
Open Source Software and its benefits for a country like Nepal.
Open Software: Lottery for Nepalese ?Arzun Bastola Class:10 I was on a seminar few months back when I used Open Software for the first time. I had heard about the Open Software before though I hadn't used. This day really was a good day for me. Had I not attended the seminar, I would just go on using the pirated Operating System. When I first knew that Linux was one of the most powerful operating system, which came complete free and an Open Source then few of my friends decided to do everything in Open Software which could be photos designing to website development. It was tough in beginning as there were no place where we could actually learn Linux. We were guided by Sagar Chhetri and Hempal Shrestha, who are working as FOSS experts in Nepal. With their help we were able to use the Linux in an important way. That is how I got involved into it. In the seminar within, I was conned about the importance of Open Software to poor people like we Nepalese. I then knew that it was a kind of lottery like to us because we shouldn't have to pay even a single coin for the softwares which were so designed that they could be used to do any kind of works as the closed softwares like Windows and others do. Open Software have very big benefit especially in a country like Nepal. The first benefit is that, Nepal still being very little exposed to the IT field compared to the western world,